There has never been a more important time to be knowledgeable about the security of your network and business. We work with several partners to provide managed security services as well as scalable security solutions for all size businesses.
Assessment Services
- Vulnerability Assessment- Leverage best in class scanning tools and techniques to identify vulnerability findings with out manual process verification and contextualization (external scan only).
- Penetration Testing- Find internal and external weakness. and gaps in your multi-layered (defense in depth) security. Identifying exploitable vulnerabilities, and penetrating as far into a your infrastructure as possible, with manual process, verification and contextualization.
- Vulnerability Insights- Leverage best-in-class scanning toolsets and techniques to identify detailed vulnerability findings, with manual process, verification and contextualization. (Internal and external in scope).
- Web Application Vulnerability Insights-Harden your distributed perimeter by assessing the vulnerabilities and security of your mobile and web layers.
Managed Security Suite
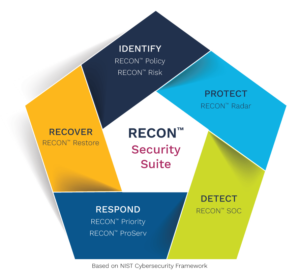
Red Echoes Tech partners with multiple providers and vendors to give options and scalability to all types and sizes of businesses. The RECON™ Suite below is a set of subscription and consulting based security solutions designed to solve unique customer challenges covering a range of security threat vectors. There are several solutions and vendors that are incorporated in these solutions and these can be used as a portfolio to suit your companies needs or many can also be used as stand alone solutions as well.
| RECON Solution | Subscription | Description | |
|---|---|---|---|
| RECON SOC | Monthly | Provides 24×7 monitoring of security infrastructure by collecting security logs and events from servers, desktops, network devices and security appliances to identify threat and recommend how to remediate. |
|
| RECON Policy | Annual | Community-driven security by leveraging a subscription based portal to share and access a library of security policy documentation developed through hundreds of information security consulting projects. In addition, Security Colony offers vendor risk assessments and breach monitoring |
|
| RECON Radar | Monthly | Discover, fingerprint and inventory all IT and IoT devices, monitor their behavior looking for indicators of compromise or sabotage, and neutralize the threat |
|
| RECON Priority | Monthly | Prioritizes vulnerabilities specific to an organization based upon developed exploits and chatter found by searching the deep and dark web. |
|
| RECON Risk | Annual | Quantitative modeling of security risks which advises executives on financial impacts of mitigating those risks…or not. |
|
| RECON Restore | Varies | A portfolio of backup and recovery solutions which can restore a system from catastrophic ransomware or malware attacks. |
|
| RECON Services | Hourly | Security focused consulting and managed services offered by Tech Data and our trusted “services only” partners. |